Search results are opened in the separate tab Search results.
In the Search results window two panes a presented:
Search results list — on the left. It includes the Search results list toolbar.
Preview pane — on the right. It shows the detailed information for the selected entry in the search results. This pane includes its own toolbar.
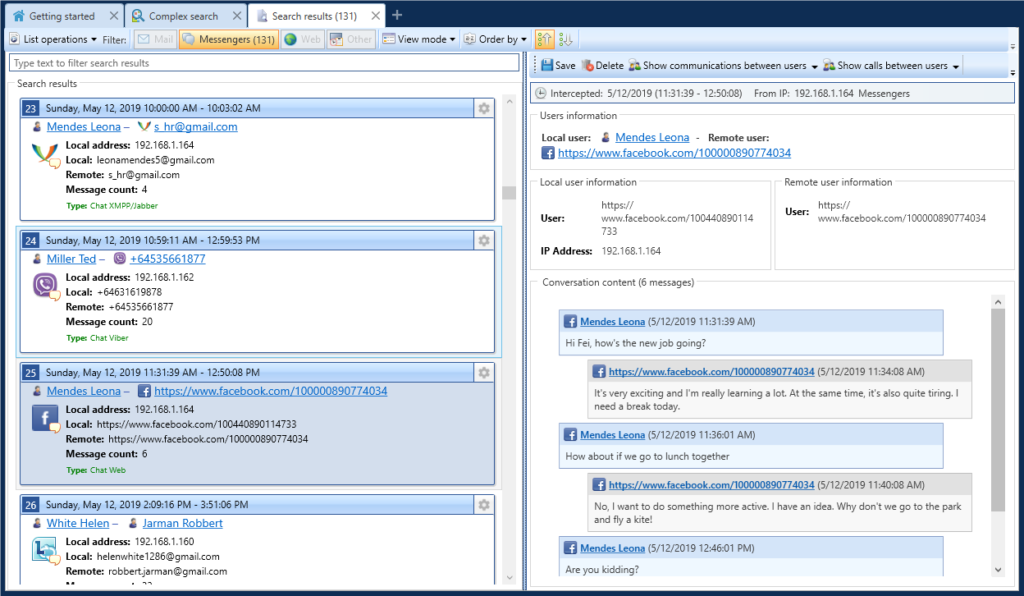
Identifying senders and recipients in search results
Each search result (entry, document) specifies local and remote users between which the data were exchanged. A remote user can be represented by a server (for example, for a document transferred over FTP protocol).
The program enforces a user card system in which each local network user is assigned with an identification card — User card, containing personal and contact user information (name and last name, job title, email addresses, user SID, ICQ UINs, user accounts in IM programs, user names in social networks, etc.).
Viewing sender/recipient information
If data were sent or received by a user with a User card assigned, the username in the link form is displayed in the search results.
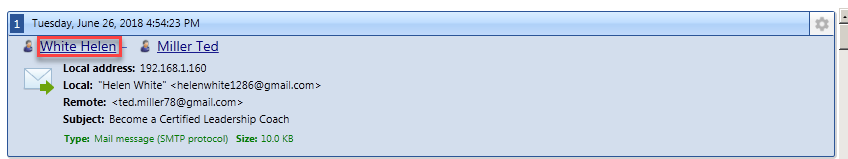
Modifying user identification information
To modify identification data of a user, click the link with a username for identified users or with identification information for unidentified users.
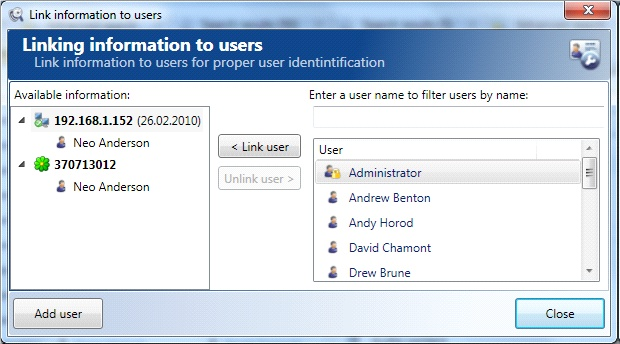
Viewing intercepted data
The program enables inspection of all the intercepted documents without necessity in opening them with external applications. For example, a PDF document may be displayed both in the program and with the Adobe Acrobat Reader application. An archive can also be viewed inside the program or opened in an external application.
The program chooses the most appropriate view mode for each document format to avoid having to view documents with external applications. For example, emails are displayed with all the main attributes (subject, to, etc.), message body and the list of attachments.
If the program doesn’t recognize the format of the document found, it will prompt the user to select one of the built-in plugins of applications intended for viewing this document formats.
- Web-traffic data (HTTP) viewing
- Viewing e-mails (POP3, IMAP, SMTP, MAPI)
- Viewing complex data formats (attachments, archives, files)
- Viewing conversations in instant messengers
- Viewing files transferred in instant messengers
- Viewing printed files
- Viewing files transferred over FTP protocol
- Viewing files copied to a storage device
- Viewing user screenshots
- Viewing endpoint activity statistics
- Viewing clipboard content
- Viewing files transferred to network shares
- Viewing cloud storages files
- Viewing keylogger
- Viewing device audit data
- Viewing recognized data
- Viewing browser activity
- Viewing results of workstation indexing
- Viewing results of search by thesaurus
- Viewing results of search by DF
Web-traffic data (HTTP) viewing
Web traffic may contain queries sent to a remote web-server over HTTP or visited URLs.
Network users can not just visit and view internet pages, but also post some information in the visited web resource. For example, they can add data in social networks, send messages in forums, blogs, or upload files, documents, archives, etc.
There are following HTTP traffic types:
- Visited URLs (HTTP)
- Data sent to a web server (HTTP POST)
- Files uploaded to a web server (HTTP POST file)
Viewing e-mails (POP3, IMAP, SMTP, MAPI)
In the email data window, you will see information blocks with the date and time of data interception, local and remote users, main mail attributes (to, from, subject), additional fields and the message content window.
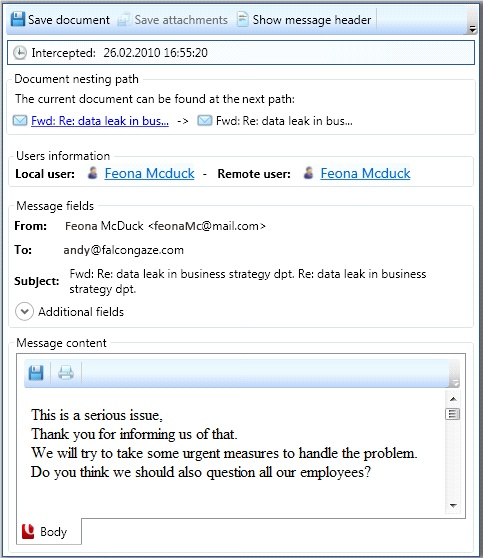
- Viewing email information
- Viewing email content
- Working with blocked message
- Viewing email attachments
- Saving an email message
- Saving email attachments
Viewing complex data formats (attachments, archives, files)
The program implements interception and viewing mail attachments that contain complex data formats. Complex format information represents documents that include data of other formats (for example, an email message may be a reply to another email message that, in its turn, contains an archive with files of various formats, etc.). Thus, a chain of various nesting levels of documents is formed, and the program intercepts, processes and enables viewing each of the documents included into this chain.
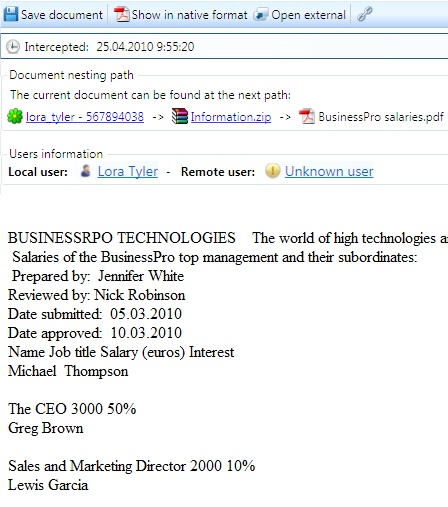
- Viewing files
- Viewing archives
- Viewing files of other nesting levels
Viewing conversations in instant messengers
The program intercepts messages and data exchanged in instant messengers (OSCAR, Viber, Jabber, Telegram, Skype, SIP, Lync, WhatsApp, Hangouts), including files transferred with the help of these programs, sender and receiver information (user accounts, UINs, avatars, contact information), conversation time, etc.
Upon viewing a conversation between certain users, one can switch to viewing all the conversations between these users for the specified period of time or all the conversations of one of these users in the current instant messenger program.
In the IM conversation window, you will see information blocks with the date and time interval of the intercepted conversation, local and remote users (user names, ICQ UINs, accounts, contact information, IP addresses, avatars, etc.) and the conversation content window.
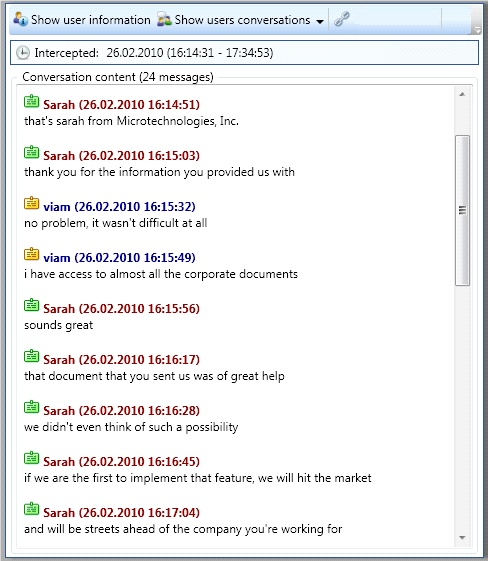
- Viewing conversations
- Viewing SMS sent from Skype
- Listening to a Skype voice call to a Skype user
- Listening to a Skype and voice call to a mobile or land line phone
- Listening to any type of SIP voice call
- Viewing all the conversations between users
- Saving an instant messenger conversation
- Printing an instant messenger conversation
Viewing files transferred in instant messengers
With the program tools interception and viewing of files transferred with instant messenger programs (OSCAR, Jabber, Telegram, Skype, SIP, Viber, WhatsApp, Hangouts) is available. Upon viewing a transferred file, you can switch to the conversation within which this file was transferred.
In the transferred file window, you will see information blocks with the date and time of data interception, data nesting levels, local and remote users and the document content window.
Viewing printed files
With SecureTower the interception of documents sent to local and network printers are available. Intercepted documents are stored in the database and displayed to the user in PDF format and as recognized text without formatting (if recognition option is activated in the system).
Viewing files transferred over FTP protocol
Network users can download files from or upload to a remote server over the FTP protocol. FTP is a protocol designed for transferring files in computer networks. The program enables intercepting and viewing files both downloaded from and uploaded to an FTP-server.
In the transferred file window, you will see information blocks with the date and time of data interception, data nesting levels, local and remote users and the document content window. In this case, the remote user is represented by an FTP-server to or from which the file was uploaded or downloaded.
Viewing files copied to a storage device
Network users can copy files to a storage device (USB flash drive, hard disk drive, optical and floppy disc). The program enables interception and viewing files transferred to storage devices.

Viewing user screenshots
When you click the screenshots icon in the user’s workday snapshot page or perform search through user screenshots, a search results window will open displaying the gallery of all screenshots taken on the selected user’s work station at specified time.
- Error messages
- Viewing mode
- Working with picture mode
- Saving screenshots
- Printing screenshots
- Viewing tips
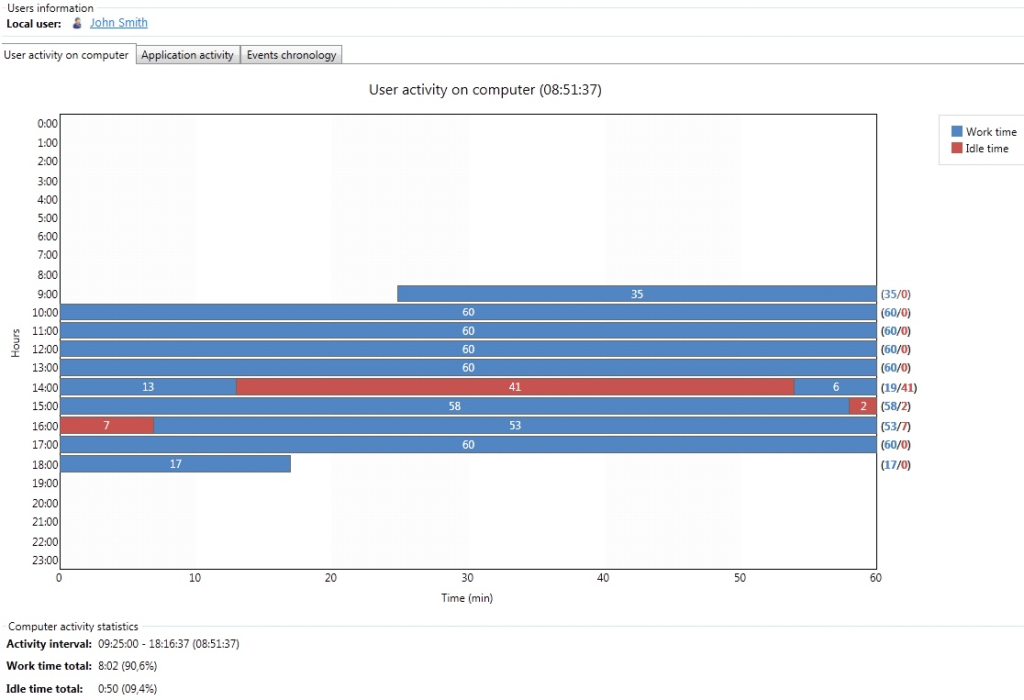
Viewing endpoint activity statistics
Endpoint activity statistics are displayed in three tabs – User activity on computer, Application activity and Events chronology.
User activity on computer
The first tab displays endpoint activity (blue) and idle (red) periods hour-by-hour. The length of the blue and red lines represents the duration of the corresponding computer state (indicated by the numbers of minutes in the lines).
Application activity
The graph shows the applications run by the user, and the percentage of time the user was working with these applications.

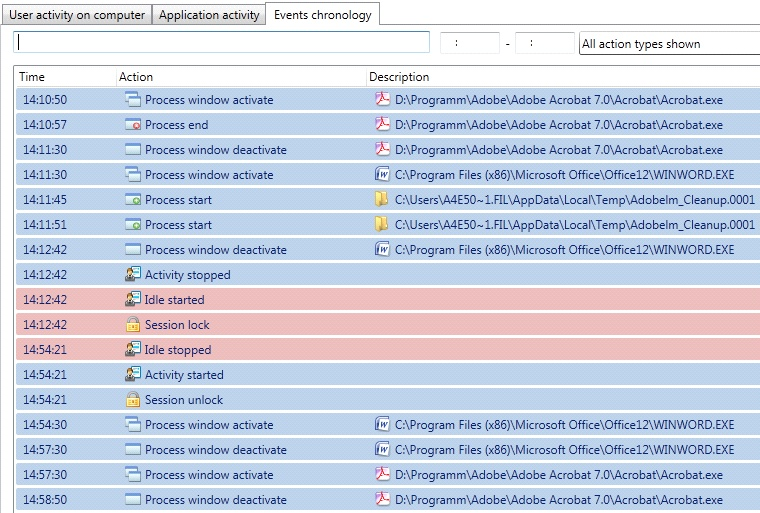
Events chronology
The Events chronology tab displays a list of all events on the selected endpoint (including start and stop of the activity and idle periods, start and termination of, activation and deactivation of application windows, etc.). The events during computer idle period are marked in red, the events in the active periods are marked in blue.
Viewing clipboard content
When you click the “N copies to clipboard” icon in the user’s workday snapshot page or perform search by desktop activity, a window with search results will be opened. There one can inspect the list of copies contained in clipboard for specified time or date interval.
Viewing files transferred to network shares
Network users can copy files to network shares. The program enables interception and viewing files transferred to network folder and discs that can be remotely accessed from another computer.
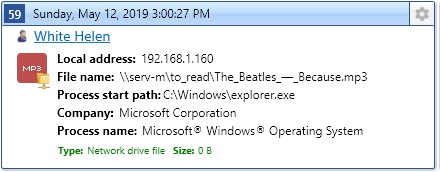
Viewing cloud storages files
Users can transfer any kind of data using various cloud storage services. SecureTower provides a complex control of operations with cloud storages for both the desktop application and web services.
The data transferred to or from cloud storages is intercepted by making a shadow copy.
If the file size is more than specified in settings for maximum size available for shadow copying only the size and name of the file, time and date of the operation and local user name will be displayed.
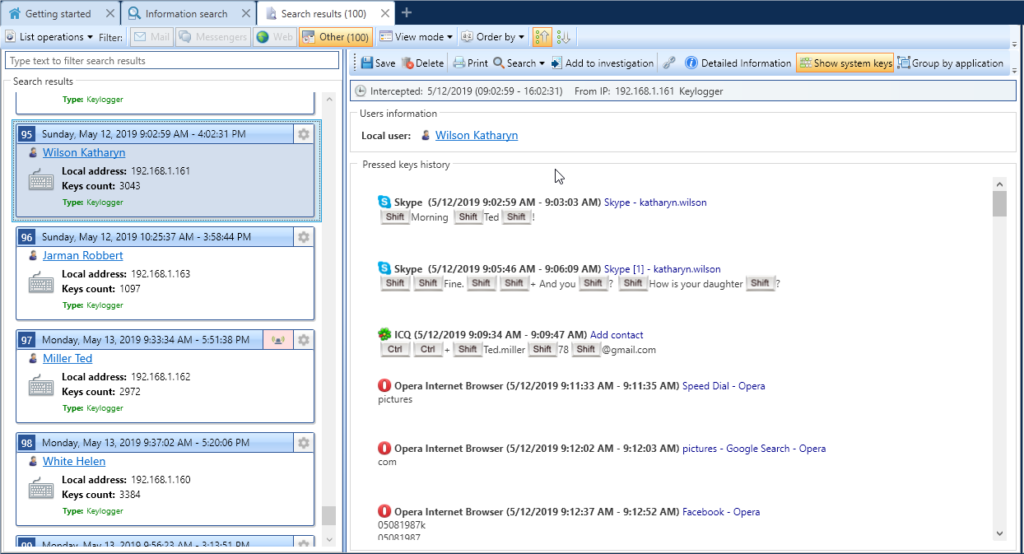
Viewing keylogger
SecureTower provides complex information about users computer activity by using keystroke logging. All data about keystrokes and corresponding applications, date and time, user IP address are available from the Client console and can be analyzed automatically in Security Policies (in case of appropriate policies setup).
Viewing device audit data
- Audit of devices usage
- File operations audit
Audit of devices usage
SecureTower enables monitoring and control of external devices usage. The number of connected devices, their types, connection duration, current condition of connection as well as local user and IP data are provided in the results window.
File operations audit
SecureTower provide a control on users and processes file operations with: mass storage devices, local network shares, cloud storages.
Viewing recognized data
The high-tech image recognition SecureTower module enables recognizing text on intercepted images with following data analysis. This functionality is useful at situations when the transmission of scanned confidential documents is widely used. The system tool works equally well with any format of graphic information (whether it is the JPG, BMP, TIFF format or any other) or PDF and DjVu files. The module recognizes data not only in
English but also in foreign languages, this feature makes it possible to carry out content analysis based on morphology.
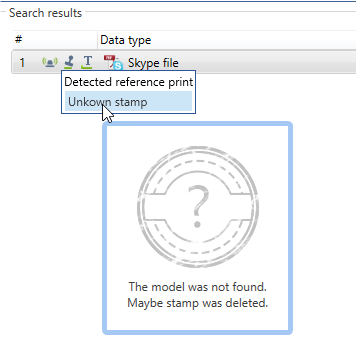
· Recognized stamps
· Recognized voice communications

Viewing browser activity
When you click the “N minutes activity” icon in the user’s workday snapshot page or perform search by desktop activity, a search results window will be opened displaying the information about the user browser activity.
- Host statistics
- Url activity chronology
- Saving reports data
- Printing reports
Viewing results of workstation indexing
SecureTower enables indexing the files systems of controlled workstations and performing match control between files on workstations and files from data bank with hashes of confidential files. If document match is detected, the system will make the corresponding record to SecureTower database.
Viewing results of search by thesaurus
The results of search by thesaurus can include not only standalone files but chats in IMs, social network posts and other types of documents that match the search conditions.
Viewing results of search by DF
The results of search by digital fingerprints can include not only standalone files but chats in IMs, social network posts and other types of documents that match the search conditions. You can open the originals of digital fingerprints while viewing the results. To open the original source file, in the search results list click Show results in the Similar fingerprints field of the result record.
